Certified Web Application Security Professional (CWASP)
 6/20
6/20
Kurs pohađalo: (17)
Početak kursa: 18.06.2019. | Trajanje: 3 dana (18 h)
Course can be paid in two installments.
About the Training:
This training course is a series of educational interactive training sessions where the attendees will gain hands on experience. They will be able to identify security flaws in web applications customized or built for the training course. They will also be able to exploit those security flaws to fully understand the value of fixing those flaws.
Audience:
- Application Developers
- Application security managers
- Security consultants
- QA testers
- IT managers
- Penetration testers
- Any security professional who is interested in learning about web application security
CWASP Certification:
Certified Web Application Security Professional (CWASP) is an exclusive certification which will test your technical skills on a live but simulated web application where you are expected to discover and exploit security vulnerabilities. Students are required to pass our online lab test in order to receive CWASP.
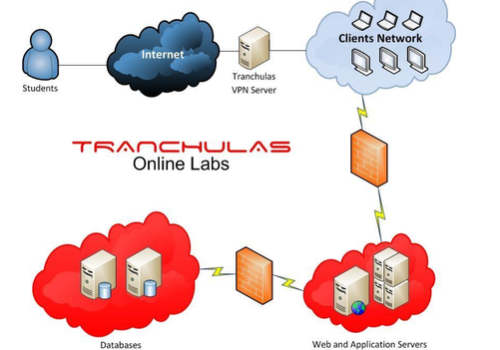
Tranchulas Online Labs:
Tranchulas Online Labs are available 24x7 for practicing web attacks learnt during training course. Online labs have several web applications based on real world scenarios which can be exploited and have different difficulty levels. Vulnerabilities include but are not limited to XSS, SQL Injection, CSRF, cookie manipulation, local file inclusion. Students are required to discover and exploit vulnerabilities in order to pass online labs and receive Tranchulas Certified Web Application Security Professional (CWASP) Certification.
Post Training Support:
You can connect with Tranchulas Online labs for 90 days to practice your hacking kung-fu after the training course. During this time our technical team will provide you email/phone/skype support in order to ensure the skills acquired on the training course are being applied correctly. This will also assist you in resolving questions that have arisen in the workplace after applying newly acquired penetration testing skills. We'll be your super hero, rescuing you from the confusion and frustration of learning.
Following topics will be covered:
- Module 1: General Concepts
- Module 2: Planning and Scoping
- Module 3: Introduction to Kali Linux
- Module 4: Information Gathering
- Module 5: Vulnerability Scanning
- Module 6: SQL Injection Vulnerabilities
- Module 7: Cross Site Scripting (XSS) Vulnerabilities
- Module 8: Improper Input Validation
- Module 9: Authentication Vulnerabilities
- Module 10: Insufficient Transport Layer Protection
- Module 11: HeartBleed OpenSSL Attack
- Module 12: Authentication Vulnerabilities
- Module 13: Authorization Vulnerabilities
- Module 14: Mass Assignments
- Module 15: CSV Injection Attack
- Module 16: XML Entity Injection
- Module 17: Browser Manipulation
- Module 18: HTML Injection Attack
- Module 19: Server Side Request Forgery Attack
- Module 20: Looking at the Big Picture
- Module 21: File Uploading Vulnerabilities
- Module 22: Assessing Application Architectures
Details of each module listed can be found in attachment below.
Pre-Requisites:
- Basic knowledge of HTML and Java Script
- Participants must bring their own laptops
Training schedule:
Monday, Tuesday, Wednesday, June 18 - 20, from 10:00 AM to 4:00 PM
Course can be paid in two installments.
Minimum number of participants is 8.



